We are expanding our identity
Dr. Nicolas Evangelos Kolonias is Professor of Art and Philosophy at Chiang Mai University. His research and doctoral work focus on the interdisciplinary study of philosophy, art, media, neuroscience, and Eastern epistemology of the mind.
We asked Nicolas to introduce us to digital identity.

“Our identity is fluid. It comes in many forms. And it changes as we become our professional, social, or sexual selves.
What is digital identity? We first need to understand how we approach the digital. As natural, as real, as fake, as representation, or as technology?
Plato presents us with an ontology of images. Objects in the physical and digital world appear as images in consciousness. Okay? Physical or digital, it does not matter.
With art, photography, cinema and computer programs, we manipulate light and information. And now consciousness has to interact with a larger system of images. We expand and become our Instagram, Twitter, or Facebook selves.
Bruce Lee says, “Be like water.” Can we be water? Yes, we can! If you pour water into a network, it will expand through it and become something new – this is our evolution.”
The identity evolution

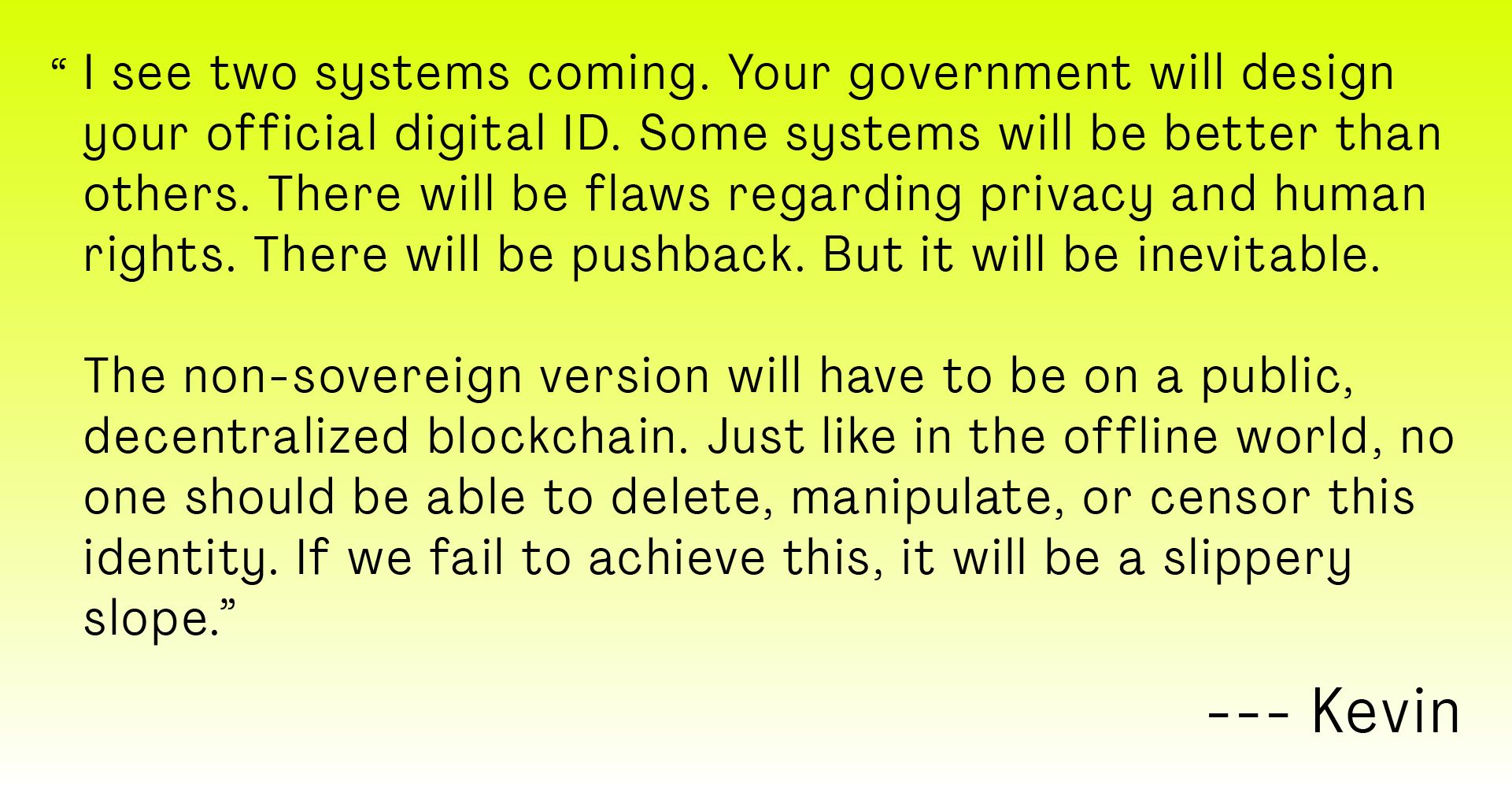
Gender, physical features, ethnicity, class, age, and nationality are identifiers that define us. Some of them are immutable. But online, identity is fluid. We have the freedom to create a new identity without the constraints of physical or environmental factors. One such identity is Kevin.
Offline a psychiatrist – online a meme and identity expert

Kevin is a pseudo-anonymous thought leader on digital identity and NFTs. We wanted to know why Kevin morphed into his Web3 persona.
“I like it because I feel like I can speak candidly about topics that I think are meaningful. I don’t want people to be able to Google my real name.
Let’s say I was on a show and someone asked me about China. Well, it’s an autocracy and it seems to be in demographic collapse.
These things are well known facts. But then if I have patients from mainland China, that might not sit well with them, and then they might not want to engage in treatment in the same way.
I don’t want my online identity to undermine my offline work. So my online identity is a meme. My PFP (profile picture) NFT was inspired by what was likely the most famous art reveal disaster of all time, Pixelmon. After the art reveal, it turned out that some art was inexpensive renderings from a video game stock asset store, not a good look. The most infamous and goofy of these was Kevin. My PFP comes from a derivative collection called Kevin Punks. I think the Kevin meme is hilarious, it represents all that is wrong and right in crypto simultaneously.”
How to design an identity system
Who we are defines the world around us. National ID cards, passports, educational degrees and certifications, issued by governments and educational institutions, help us to prove who we are. Our interaction with society forms our reputation, which exists in the memory of our community members. “In society, identity is a matter of access or no access”, says Nicolas.
Online, that memory is databases. And like identity, the technology and architecture of our digital network and memory is dynamic.
Kevin’s fluid identity allows him to be part of a Web3 community and pursue his career as a psychiatrist.
Top-down, sovereign, centralized ID
State-issued identity documents give us access to travel, education, public and financial services. But according to the World Bank, 850 million people still lack government issued identity documents.
As a result, entire populations are vulnerable to abuse and even slavery. But having documents only on paper can be an elusive security. Almost every human trafficking story begins with a trafficker taking away a victim’s passport, preventing them from seeking help.
To address this, the United Nations set out an ambitious target in its Sustainable Development Goal 16.9, which states: “all people will be able to obtain a “legal identity” by 2030 (SDG 16.9).”
The UN has since recognized the importance of digital identity and has incorporated it into this goal.

Well-designed legal identity empowers individuals with consent-driven creation. It facilitates time savings in government services, enables secure healthcare record sharing, and minimizes identity fraud.
At the same time, it ensures individuals have knowledge and control over their personal information.
But even the best of government ID systems have their flaws.
The risks of centralized ID systems
Estonia is often touted as the most successful example of a transition into a digital government.
More than 98% of the population have electronic ID cards that they can use to vote, pay taxes, and access government services online.
In 2017, Estonia discovered a security vulnerability in the cryptographic keys of approximately 750,000 Estonian ID cards. This vulnerability had the potential to compromise users’ private keys, making their ID cards open to identity theft.
The Estonian prime minister took decisive action by disabling the certificates of the affected ID cards and issuing updates to the certificates. These measures were crucial to mitigate the potential consequences of the security flaw.
“But the fact that the government has the power to disable someone’s ID certificates is terrifying.”, Kevin adds.
In fact, a centralized ID model is a dream for autocratic and authoritarian regimes, especially when coupled with biometric authentication software. Uganda is an example of what can happen when ID systems are in the wrong hands.
Uganda’s ID Program Violates Citizens’ Rights to Privacy and Autonomy
In Uganda, journalists receive “threats from anonymous sources regarding their journalism work”, says a report of the African Centre for Media Excellence. This is due to the fact that the country’s biometric and digital identity programs work in tandem with real-time surveillance capabilities to monitor journalists’ communications.
This and other similar examples from governments known for human and civil rights infringements underlines why many are concerned about the inherent lack of privacy that is almost built-in to digital identities.
Privacy also plays a critical role in our digital, non-sovereign IDs. Those applying for a US visa, for example, must now also supply their social media information to the authorities along with sovereign ID documents. Our social media is now also a matter of access or no access.
Your passport and Facebook account, please
In recent years, many have voiced concerns about how big social media companies use and store our personal information. Indeed, in 2022 Meta generated nearly $114 billion in advertising targeted to our identities in 2021.
The story is old, but the problem remains unsolved. Google, Twitter and Meta, centralized and gated services, continue to own and control our identity data, retaining the ability to manipulate and delete it. Those who leave the platform lose access to their network, their data, and their identity.
But that doesn’t worry Nicolas. “What will happen? Technology will create a system that will push the boundaries again. So we will create a system of blockchains as an alternative system of access. Then the government will come and try to regulate it. It’s always a process of expansion, regulation, and expansion and regulation…”
Bottom-up, self-sovereign identities (SSI)
We asked Kevin what this alternative system could look like.
“Imagine. You have a crypto wallet on your phone that is specifically designed for your identity. Your wallet serves as your decentralized Web3 identifier. Similar to a social media account, but not tied to any single platform. Your wallet gives you access to the data you create in Web3. You authenticate it with your private keys, much like a password, and the tiny details of your history are stored on a public blockchain to create a completely customized and targeted online experience.
Anyone can create these wallets without permission from a central entity.”

Use cases of digital identity
Decentralized, private, monetized social media
For Kevin, identity on the blockchain is about ownership and control of our personal data, but also about taking charge of the monetization of that data. He explains: “You can move between social media platforms and take all your followers with you. You own your decentralized social graph. You can earn revenue from the engagement you drive to the decentralized social media platform.
This system allows you to build your digital reputation based on your past actions and find others based on proven shared experiences. Others can follow and message your wallet.
You express your reputation and identity through attestations. Attestations can take the form of non-transferable (soulbound) tokens. These tokens serve as proof of event attendance, showcase your decentralized finance (DeFi) borrowing history, or demonstrate your contributions to a community.
We can also tokenize medical records, driver’s licenses, and university degrees. Governments could even issue legal identity documents.
It’s a new and better form of access because you control your data, which is immutably stored on the blockchain. Nobody can take it away from you.
All of this can be performed without revealing the identity data attached to our wallet, or even the individual soulbound tokens themselves.
This is because soulbound tokens can be gated behind zero-knowledge proofs. Therefore, this individual data that makes up your social graph does not have to be visible to the public. You can choose to reveal it on a case-by-case basis.”
Examples of Web3 identity projects
IDNTTY – A public infrastructure layer that enables decentralized digital identity. Once set up, users can sign documents on the go within the IDNTTY application while maintaining control of their private information.
XMTP – The protocol enables secure in-app messaging and payments between Web3 wallets, both within the same interface. Coinbase Wallet is the first wallet to join the XMTP network.
Backpack – Backpack is an asset and protocol agnostic Web3 wallet that integrates executable NFTs (xNFTs). xNFTs can gate experiences (xNFT decentralized applications) that can run within the Backpack wallet itself. Because of its ease of use, Kevin believes that Backpack could be Web3’s “iPhone App Store moment”.
Streamlined KYC, identity theft prevention, and regulatory compliance
A blockchain-based identity design would also play a role in online security and compliance.
In most jurisdictions, opening a bank account requires us to send pictures of identity cards and passports over the internet. The more copies we send, the less secure we are.
“If your ID is floating around on the Internet, that’s a big problem. Fraudsters use it to apply for bank accounts and even credit cards. That is the scary thing about a system that relies on photos and scans that can be easily copied.”, says Mike Verwaal, a Fraud Manager at a FinTech company.
Scary, indeed. In 2021, 15 million U.S. consumers became victims of identity fraud. The losses amounted to $24 billion.
A form of digital ID would not only eliminate this form of identity theft, but it would also streamline know-your-customer (KYC) processes. In India, e-KYC reduced the costs for authenticating customer identity by 86%.
Human intelligence, artificial intelligence and democracy
The growing use of AI is another reason to look at how we can create fully verifiable digital identities using blockchain technology. This is because, in the online world, we connect with all sorts of humans and their identities, but also with lots of bots and AI.
Kevin adds: “We know that extreme opinions get the most attention on the web. Inflammatory content drives views. Bots take those opinions, pump them up, and make them go viral. It makes society look like we don’t agree on things. It looks like society is falling apart.
72.7% of Donald Trump’s followers on Twitter were estimated to be fake by an online tool, Sparktoro. I strongly believe that he would not have won the 2016 election without Russian interference. The election was extremely close, he won at the margins, and I do believe that Russia’s bots and microtargeting made possible by the Cambridge Analytica scandal put him over the top.
AI and deep fakes will only make this situation worse. But bots and AI don’t go to concerts, people do. And with decentralized identity, it would be easy to tell if a profile was a human or a bot by seeing if this person has gone to some kind of real-world event. We now have the ability to massively reduce the number of fake accounts on our social media platforms.”
Through what seems like a trivial example, Kevin highlights one of the most valuable things a blockchain-based digital identity offers: real-world use cases. In a world where people are increasingly forming their world views (and voting intentions) via what they see on social media, the creation and integration of verifiable digital identities is perhaps one of society’s most important tasks.
Epilogos
On April 27, 2023, Shanghaiist titled: “Tencent Cloud Launches Affordable Digital Human Production Platform.” Deepfakes-as-a-Service – for $145.
November 5, 2024, is set for the next presidential election in the United States. According to Kevin, Joe Biden’s Twitter account counts only 43% bots.
Digital identity is more than a meme. It’s part of our evolution. We better get it right.